Smart Integration Connector supports two different types of whitelisting. You can whitelist traffic from the internet to your environment or from the internet to the Azure Relay Service.
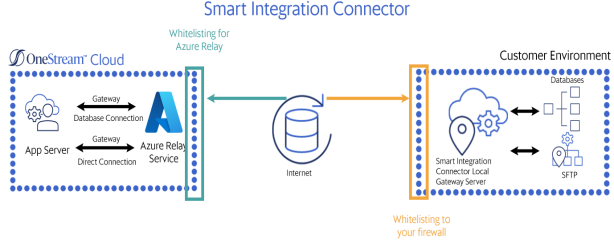
Whitelist the Azure Relay to your Firewall
The best practice is to whitelist the Azure through a “*.servicebus.windows.net” domain or using the fully qualified domain names for your specific Azure Relay namespaces.
-
(Best Practice) To limit traffic from your Azure Relay namespace:
-
Add the namespace <*.servicebus.windows.net> or to your firewall rules, or:
-
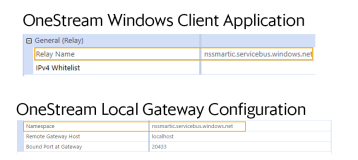
To whitelist through the full namespace, go to System > Administration > Smart Integration Connector and click Relay at the top.
-
The Relay Name is the namespace of the Azure Relay. Add this namespace to your firewall rules to restrict traffic from this Azure Relay. The namespace should have a format similar to this example: <somehost>.servicebus.windows.net.
-
NOTE: The namespace will be different for your development and production environments.
-
Additionally, you can limit traffic further from an IP address by following these Azure-specific instructions:
Whitelist traffic to the Azure Relay
You can limit Azure Relay to only accept traffic from certain IP ranges.
-
Set the outbound port to 443. This port needs to be fully open outbound to communicate with the Azure Relay.
-
From the OneStream Windows Application client go to System > Administration > Smart Integration Connector > Relay.
-
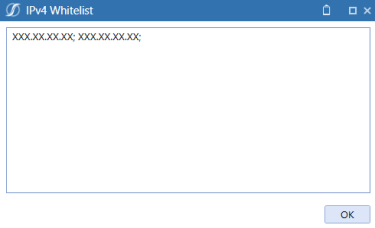
Select IPv4 Whitelist.
-
Enter IPv4 compatible IP (XXX.XXX.XXX.XXX) or CIDR addresses (XXX.XXX.XXX.XXX/XX) separated by a semi colon in the IPv4 Whitelist dialog box.
NOTE: IPv6 addresses are not currently supported.
NOTE: Do not include any extra spaces for characters.
-
Restart your Local Gateway Service.